Identity-First Security without compromise
Veridium’s Identity Assurance Platform—equipped with AI-based identity threat protection and continuous authentication capabilities—resolves a foundational security challenge that is critical to the effectiveness of nearly all other security controls related to user identity and access management: ensuring accurate user authentication, from start to finish.

Unique Person-to-Device Bonding

Compliance and Regulatory Framework

Integrate with platform and security software

Active and Passive Biometrics

Bridging to Cloud-first & EntraID
Survival of the Fittest: Allianz Taps Veridium for Cutting-Edge, Password-less Cybersecurity Defense! Identity is the new attack surface and Allianz selected Veridium as their first line of defense against cyberattacks.
Veridium’s unique solution provides Allianz’ users with a seamless and consistent passwordless experience for VPN/Radius connections, VDI infrastructures/thin clients, mobile devices, BYO devices, and legacy apps
By implementing Veridium’s solution, their IT teams are delivering passwordless experiences that remain consistent regardless of the device, location, application, or networking connection being used – such as VPNs with Radius.
Your Partner for Passwordless Authentication
Veridium is the most comprehensive Integrated Passwordless Platform powered by AI-based Behavioural Biometrics
We Work With the Best in the Industry
Veridium is the most comprehensive Integrated Passwordless Platform powered by AI-based Behavioural Biometrics




















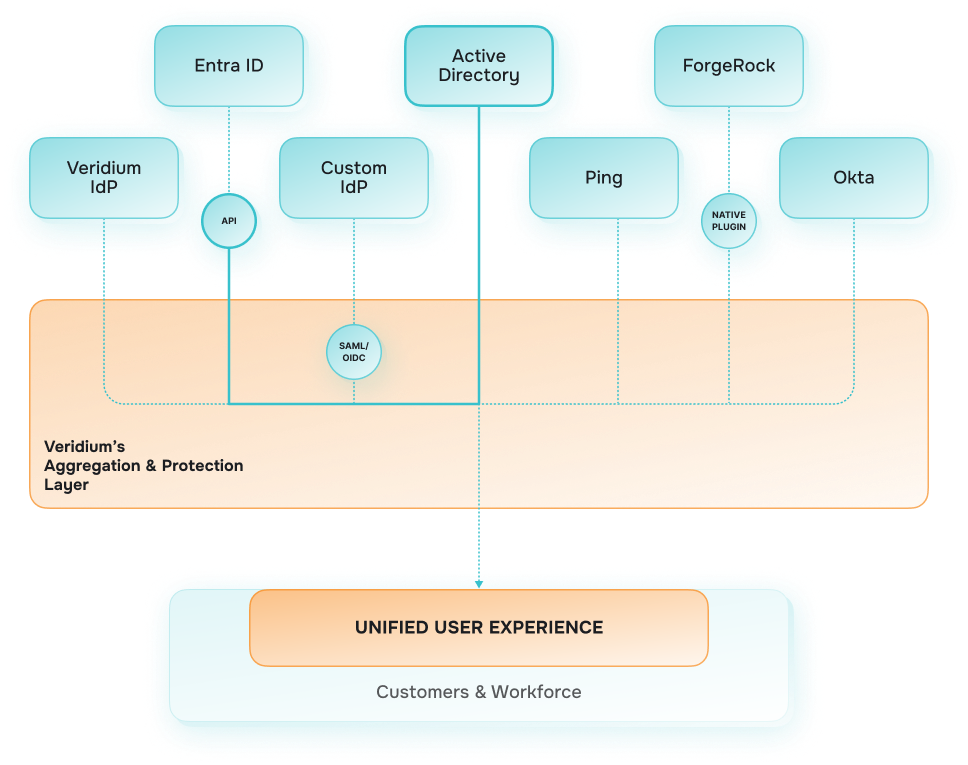
Veridium’s Multi-Cloud
and Protection Layer
Veridium allows you to give your workforce and customer base consistent user experience and is able to protect your system with precise AI-anomaly detection. There is no vendor lock in.
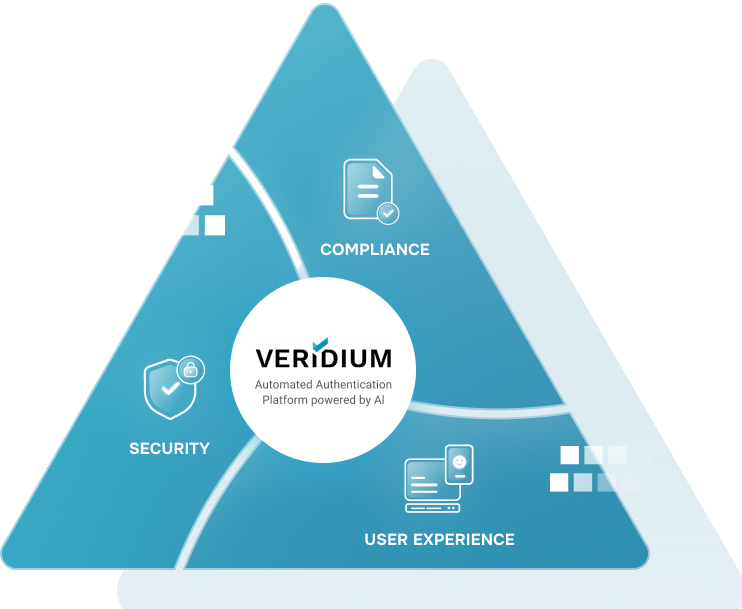
For a Passwordless World
Veridium is the most comprehensive Integrated Passwordless Platform powered by AI-based Behavioural Biometrics, enabling:
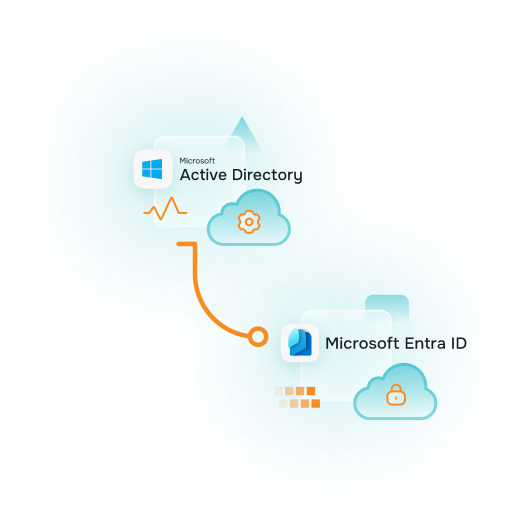
Bridging you to Cloud-first
Use the power of Veridium on-prem or hybrid. With our Identity Platform you dont need to comprimise with state of the art identity software.
True On-Prem Identity Management with Veridium
With Veridium you can bridge your cloud-first implementation from Active Directory to Entra ID and cloud first security with ease.




Passwordless MFA Platform
Veridium is the most comprehensive Integrated Passwordless Platform powered by AI-based Behavioural Biometrics, enabling Multi-Factor Authentication (MFA)

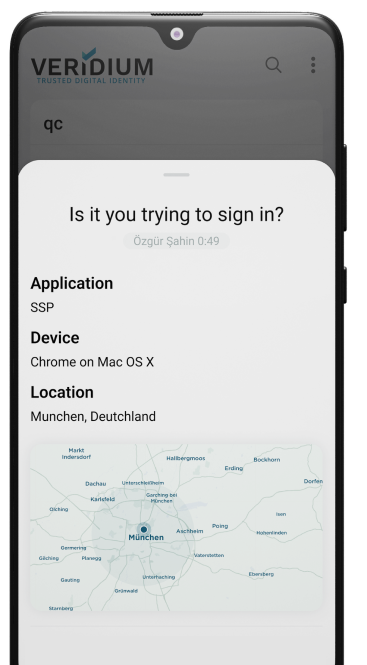
Why Veridium?

Bio-to-Device Bonding
Our unique Biometrics-to-Device Bonding protects against sophisticated identity thefts

Paired Active and Passive Biometrics
We combine the environment and behavior of a person with the biometric identity characteristics

Intelligent Login Protection
Our patented Anomaly Detection defends your environment against wide range and spear attacks

Orchestrator & Regulatory Framework
We deliver a Zero Knowledge Orchestrator, as well as a easy to use regulatory and compliance framework.

Great User Experience
Our Products are designed to not compromise with the user experience

SIEM / SOC Integration
Our Intelligent Login Protection integrates with your SIEM Tools.
We Integrate With your favorite Apps and Platforms
Veridium uses the full potential of protocols and APIs to bring security and consistent user experience to your applications