A Strategic Imperative: Digital Sovereignty for Identity Authentication
Authentication processes take place within national borders and under full control of organizations that wish to achieve Digital Sovereignty.

Introduction
Authentication and Digital Sovereignty
As organisations navigate an increasingly complex security and regulatory landscape in an Identity-First world, the need for digital sovereignty for identity authentication and management has become paramount. Governments and industries worldwide are imposing stricter data localisation mandates, forcing organisations to reassess their reliance on global cloud authentication providers. Organisations that fail to comply risk regulatory penalties, data exposure, and reputational damage.
Veridium’s authentication solution with AI-based Identity Protection is designed to help organisations achieve compliance while improving security, ensuring that authentication processes remain within national borders and under the full control of the organisation.
Understanding Digital Sovereignty in Authentication
Digital sovereignty refers to the requirement that an organisation’s critical data – including user identities, authentication credentials and access logs – be stored, processed and secured within the legal jurisdiction of the country in which it originates. This is in response to growing concerns about foreign government access, supply chain dependencies and vulnerabilities in third-party clouds.
For organisations operating in regulated sectors such as finance, healthcare and government, maintaining a sovereign authentication strategy is not just a compliance requirement – it is a competitive advantage.
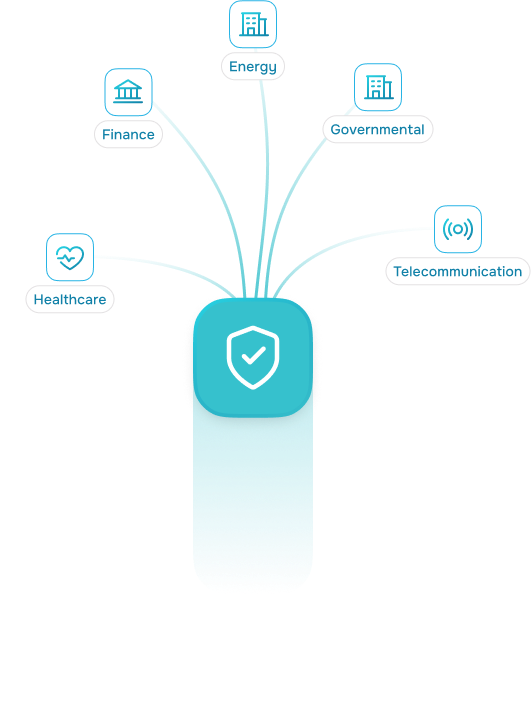

Global trends driving the need for locally hosted authentication
Regulatory mandates by country
Impact on Industry Sectors

Financial Services
Banks and fintech providers must ensure that authentication credentials remain within the country of operation.

Healthcare
Patient identity verification and authentication solutions must comply with strict local privacy laws.

Public Sector
Government agencies require sovereign authentication to protect sensitive citizen and defence data.

Critical Infrastructure
Telecommunications, energy and defense sectors prioritize on-premises authentication to mitigate cyber threats.
How Veridium Supports Digital Sovereignty Initiatives
Veridium offers a highly flexible authentication platform with built-in, AI-driven identity threat detection and response capabilities that supports both on-premises and sovereign cloud deployments, enabling organizations to meet data localization objectives and requirements without sacrificing security or user experience.
Key Features
Why Organizations Choose Veridium for Digital Sovereignty Initiatives
Regulatory Compliance

Supports compliance with GDPR, FedRAMP, RBI and other sovereign cloud regulations.
Enhanced Security

Reduces the risk of foreign government access to user identity and authentication data.
Enterprise Control

Ensures that organizations maintain full control over their authentication infrastructure.
User Experience

Provides frictionless authentication without compromising security or user experience.
Future-Proofing
Authentication
As governments tighten regulations around data sovereignty, organisations must take proactive measures to localise authentication processes and increase control over identity management. By deploying Veridium’s authentication solution, organisations can meet these evolving compliance requirements while increasing security and user confidence.
Now is the time to future-proof your authentication strategy with a sovereign-ready authentication solution that balances compliance, security and innovation.
Contact Veridium today to find out how we can help you implement a sovereign authentication strategy tailored to your business needs.