Zero Trust and Identity-First Principles
Embrace a robust security posture with Zero Trust and Identity-First strategies from Veridium. Adopt Veridium’s comprehensive approach to security that prioritizes identity verification and continuous monitoring.
Implementing Zero Trust Security
Implementing Zero Trust and Identity-First strategies helps organizations comply with stringent regulatory requirements such as GDPR, HIPAA, PCI-DSS and NIST guidelines. Veridium’s flexible platform allows IT administrators to easily configure policies and workflows to meet evolving security needs and compliance standards. The adaptability of Veridium’s solutions ensures that organizations can respond quickly to new threats and regulatory changes, maintaining a secure and compliant environment. By adopting these strategies, businesses can safeguard their digital assets while providing secure, seamless access for users.
Accelerometer and gyroscope of phones are used

Measure user- smartphone- computer-relation
Stronger Identities with Risk Signaling
Build with full confidence
and Zero Trust – Veridium
Read our Fact Sheet

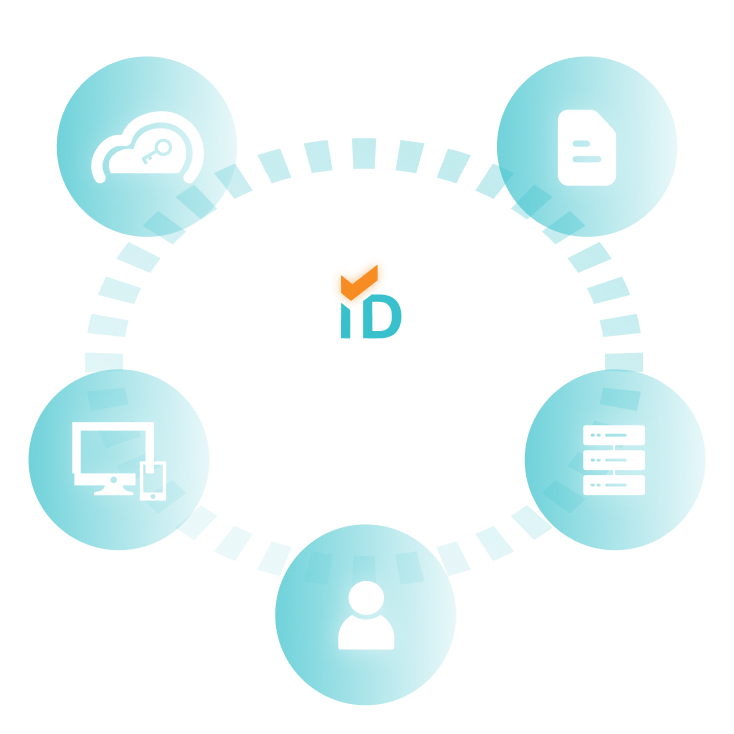
Identity Assurance Platform
Insurance
Explore how Allianz Group enhanced security and streamlined user experience with Veridium’s Zero Trust authentication. See the case study now.

4F-ID Verification
Discover how the Hamburg police use Veridium’s 4F ID technology for fast, reliable fingerprint identification in the field. See the case study now.

4F-ID Verification
Cuy Móvil Revolutionizes SIM Card Registration with Veridium 4F-ID Technology. See the case study now.

Identity Assurance Platform
- Financial Institutions
Learn how Six Group leverages Veridium’s cutting-edge solutions to enhance security and streamline authentication processes. See the case study now.
Business Value & Use Cases
Advanced identity management solution
Identity-First Security Approach
The Identity-First strategy prioritizes identity as the primary security perimeter, shifting the focus from traditional network-based security to user-centric authentication. Veridium’s advanced identity management solutions integrate seamlessly with existing infrastructures, providing secure and frictionless access to applications and data. By leveraging biometric verification and AI-driven anomaly detection, Veridium ensures that user identities are continuously validated, preventing unauthorized access and reducing the risk of credential-based attacks. This approach not only enhances security but also improves user experience by simplifying authentication processes.

“never trust, always verify”
Zero Trust Security Model
Veridium’s Zero Trust strategy operates on the principle of “never trust, always verify,” ensuring that every access request is thoroughly authenticated and authorized. By continuously validating the identity of users, devices, and applications, Veridium minimizes the risk of unauthorized access and potential breaches. This approach involves stringent authentication methods, such as biometrics and multi-factor authentication (MFA), to ensure that only legitimate users gain access to critical resources. The Zero Trust model also emphasizes the importance of monitoring and logging all activities, providing real-time insights into potential security threats.
Digital Sovereignty in Multi-Cloud Environments
Identities are the most sensitive data in an organization; should you entrust all
identities to the cloud?

Repatriation involves returning sensitive data from the cloud back to on-premises systems for enhanced security.