Composer
Challenges of the IAM Teams
- Multiple IAM Solutions.
- Providing a consistent, omnichannel user experience across individual applications is becoming increasingly difficult.
- Spiraling application development costs, with operational support teams, often reliant on developers to manage changes and incidents.
- Detecting & responding to cybersecurity threats is not a single vendor solution and requires collaboration between business-critical systems.
- Inability to dynamically change the user experience without code changes, leads to a poor customer experience and retention problems.
- There might be an insider threat in place

Solution: VeridiumID Composer
- Real-time orchestration enables a seamless, transitional customer experience across web, mobile and call centre.
- External risk scores drive the customer experience, ensuring a fully integrated with existing fraud detection & SOC solutions.
- Pivot end-user experience rapidly, without any application-level code changes.
- Intuitive user Interface offering wizard-driven and drag-and-drop workflows, accommodating the novice and experienced users.
- Standards Based Policy Expression – OPA (Open Policy Agent) and Rego support a programmatic approach to defining rules.
- Remain IAM Agnostic, supporting the multi-cloud application strategy.
- Behavioural biometrics enhance a strong authentication strategy, increasing security without disrupting the end user experience, negating the requirement for a traditional risk-based approach to security.
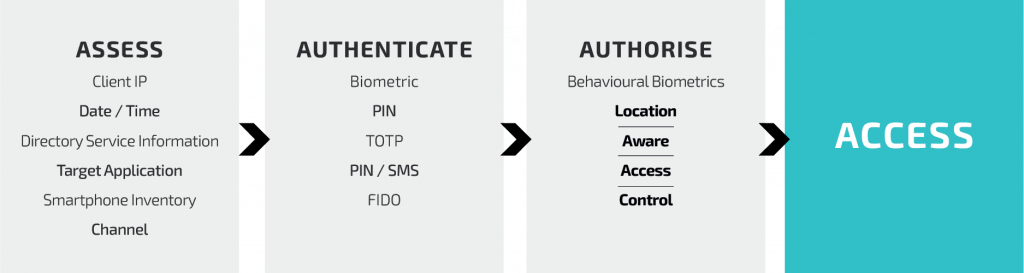
Benefits for Enterprises
● Improved customer satisfaction by providing a consistent authentication experience across mobile and web channels.
● Fewer developers are required to implement & maintain authorisation rules within individual applications, leading to staff cost-savings.
● Administrators, expected to manage authentication workflows across many, enterprise applications can do so from one central source, which improves productivity and employee satisfaction.
● Enterprises gain greater insight into cybersecurity trends, detect anomalies and prevent incidents with a holistic, end-to-end view of all authentication events.
● Known vulnerabilities can be addressed swiftly, enterprise wide with minimal end user friction, avoiding reputational damage and achieving regulatory compliance.

Related Resources

What Organizations Need to Know About Passwordless Authentication
Download Whitepaper

Case Study
Global
Swiss Bank
Watch Now